Detailed Results in DAST
The Detailed Results tab shows information about each detected vulnerability. To switch between the issues of different scans, use the scan list in the upper-right corner.
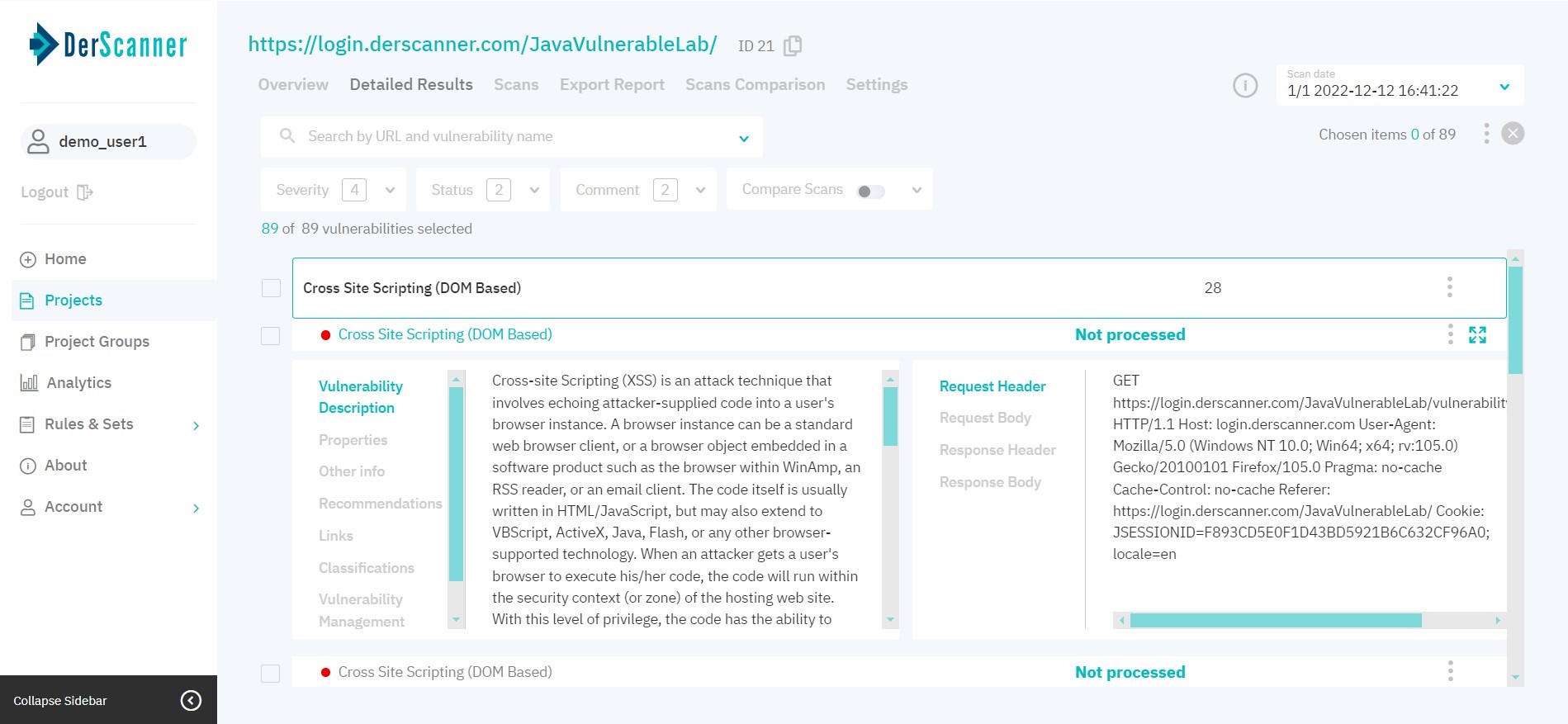
Figure 6.4: Detailed results
By default, vulnerabilities are grouped by type. To facilitate navigation, type a URL or vulnerability name in the search bar, or use filters (fig. 6.5).
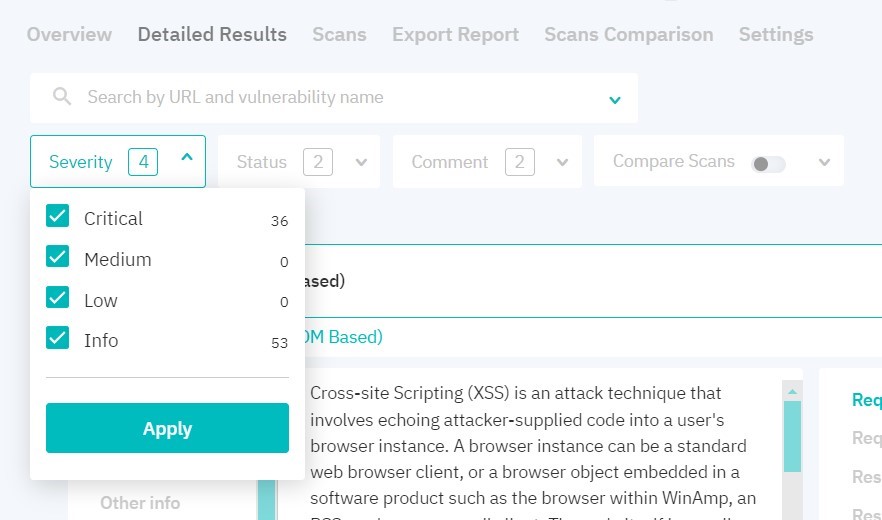
Figure 6.5: Results filters
You can filter results by the following parameters:
- severity
- status
- comment
- if there are two or more successful scans in a project, you can compare the current scan with any of the previous ones and display vulnerabilities according to status:
- new — display new vulnerabilities compared to the scan selected from the list
- remaining — display the vulnerabilities found in both scans
- fixed — display vulnerabilities detected in the scan selected from the list but not found in the current scan
Filters will be applied after you click Apply.
By clicking on the three dots to the right of the package or a specific vulnerability, you can change their severity level and status. When changing vulnerability status and severity level, security score is recalculated. Vulnerabilities with the Rejected status are not taken into account when calculating vulnerability number and security score. When rescanning, vulnerability statuses are saved.
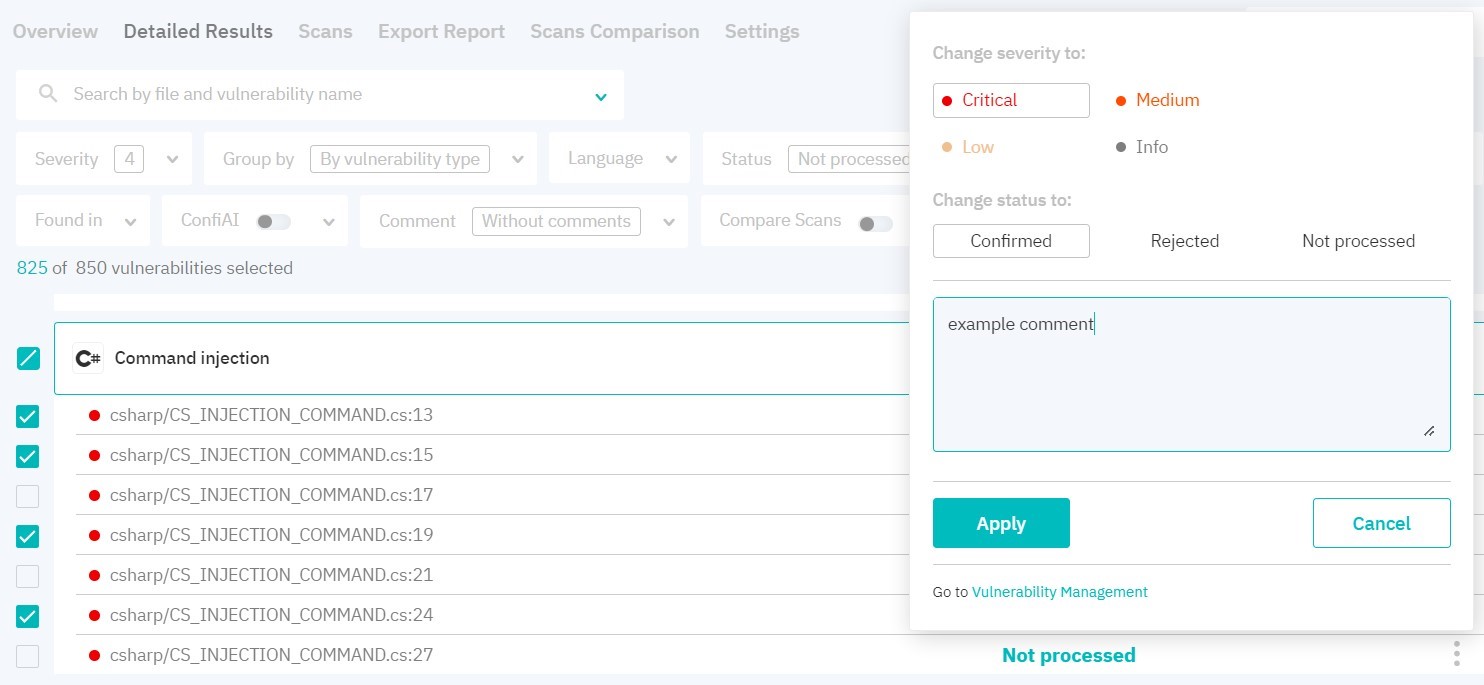
Figure 6.6: Vulnerabilities pack management
After choosing a vulnerability entry, the bottom part of the page displays the respective header/body pairs for the request and response. To view information about the vulnerability in full screen, click the icon in the upper right corner. The above will show information about the chosen vulnerability: Description, Properties, Other Info, Recommendations, Links, Classifications, Vulnerability Management and Task Manager.
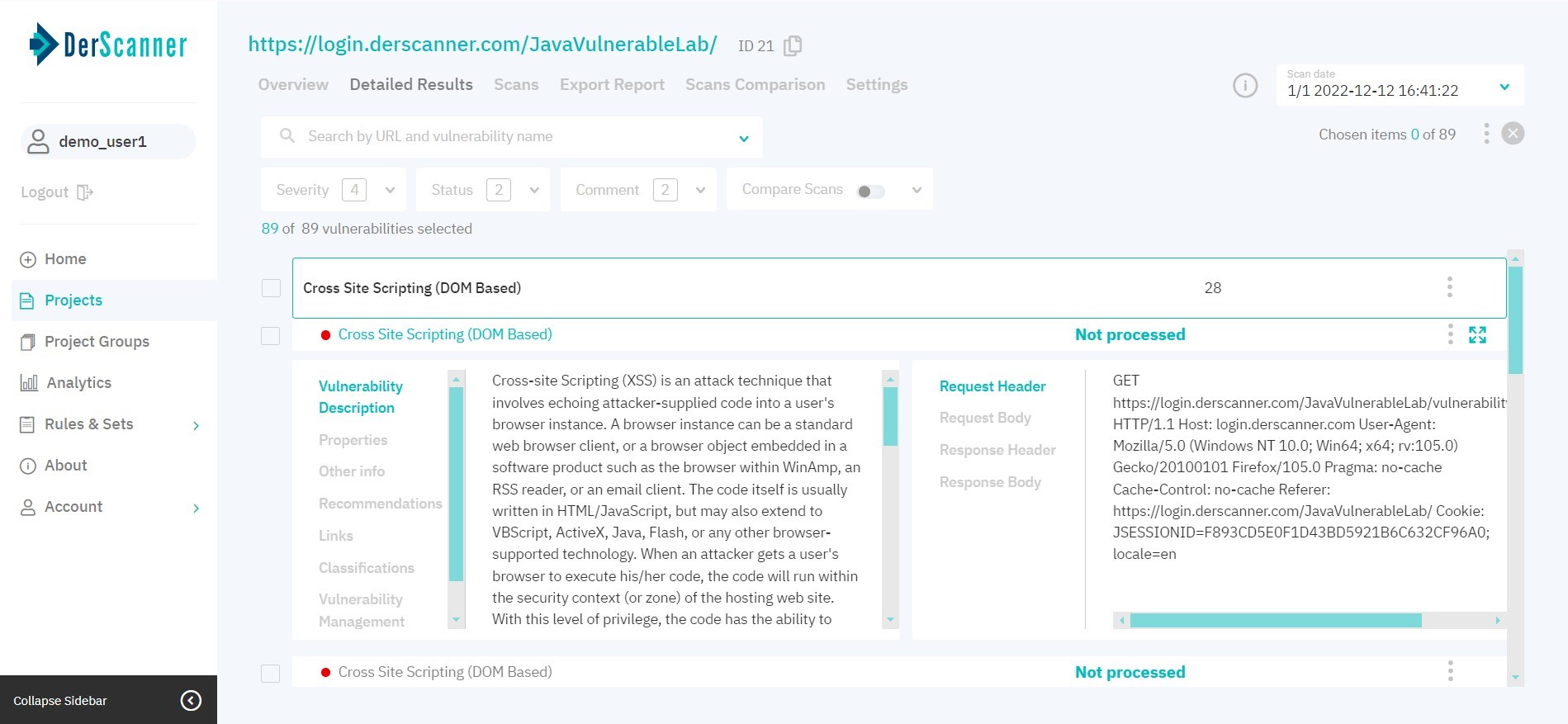
Figure 6.7: Vulnerability Properties
The Classifications (fig. 6.8) tab displays respective items from CWE, WASC, OWASP Top 10 2017, OWASP Top 10 2021 and WSTG-v4.2.
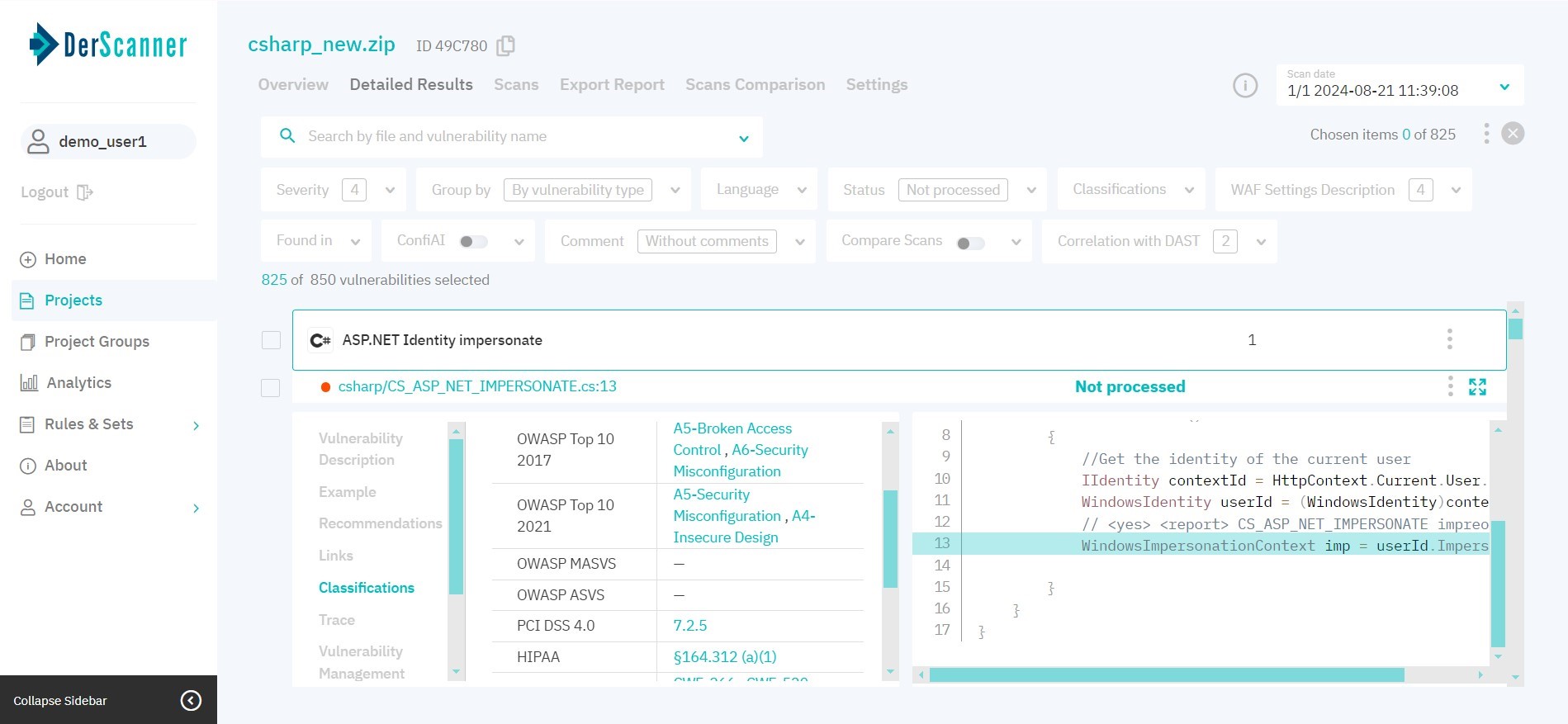
Figure 6.8: Classifications
In the Vulnerability Management tab (fig. 6.9), you can change the severity level and status, add a comment to an entry, or view the event log with actions and comments left earlier.
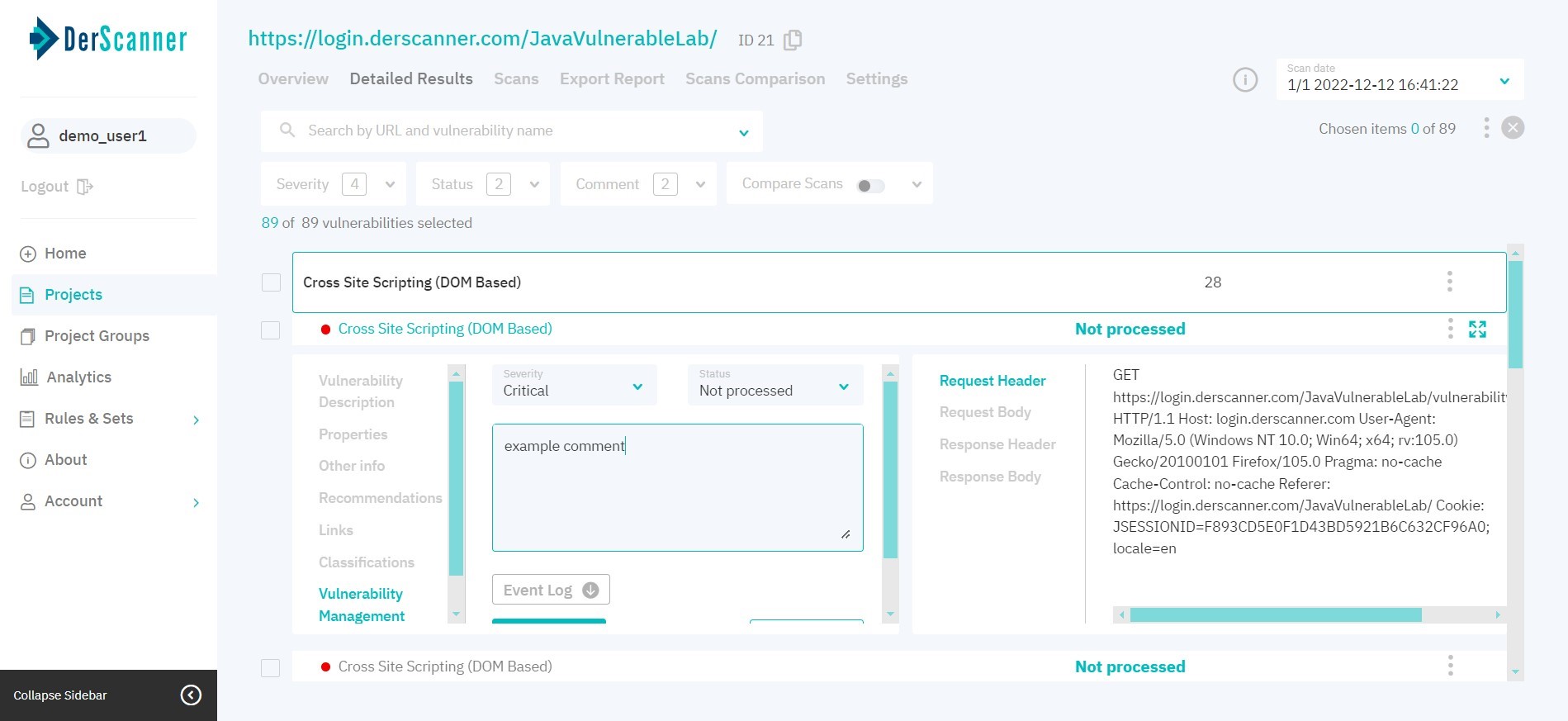
Figure 6.9: Vulnerability management