Detailed Results in SAST
The Detailed Results tab shows information about detected vulnerabilities. To switch between different scans, use the scan list in the upper-right corner.
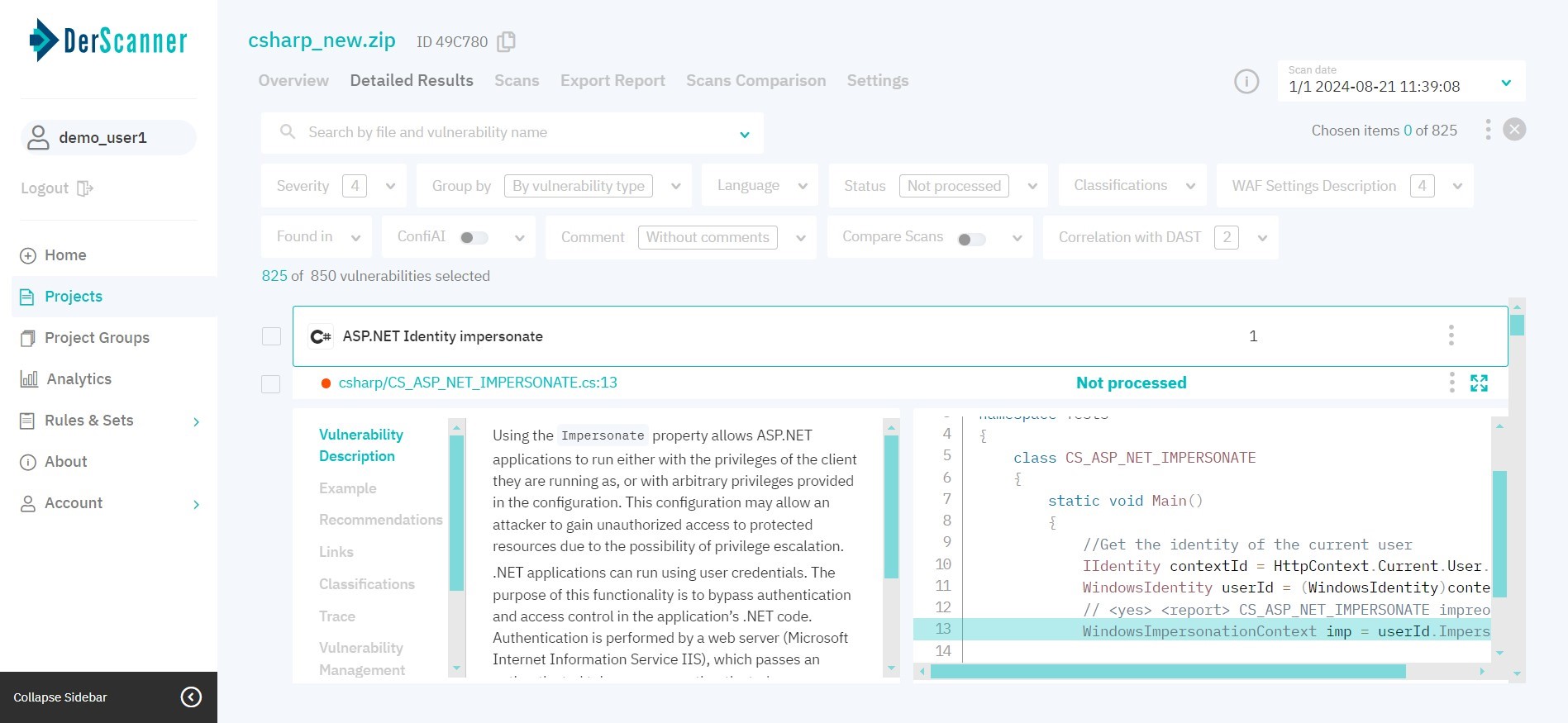
Figure 5.7: Detailed results
By default, vulnerabilities are grouped by type. You can also choose to group vulnerabilities by other parameters:
- file
- sink
- source
- package
To facilitate navigation, type a vulnerability name in the search bar or use filters.
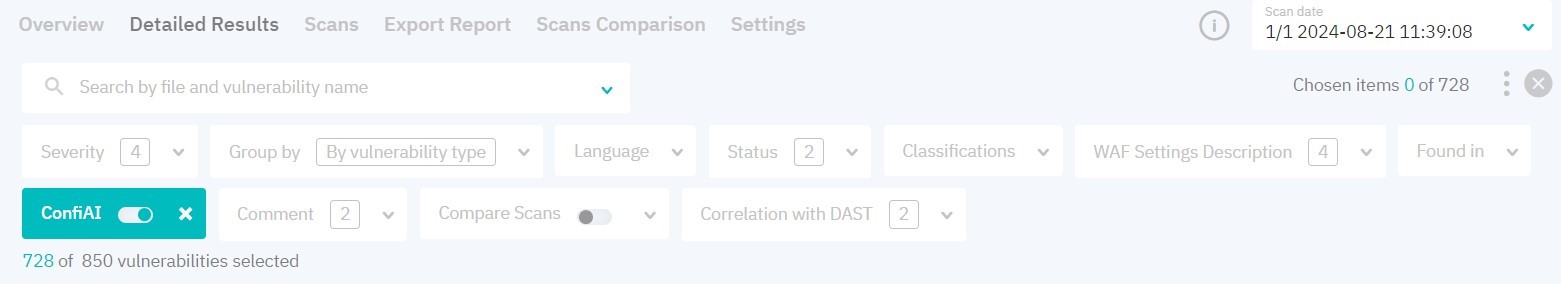
Figure 5.8: Results filters
You can filter results by the following parameters:
- severity
- programming language
- status
- classification
- availability of WAF set up instructions
.classfiles vulnerabilities- comment
- linked Jira tasks
- enable ConfiAI with one of the following modes:
-
only true — displays vulnerabilities with a high likelihood of being true positives
-
only important — displays vulnerabilities that need immediate attention
-
custom — allows you to adjust the sensitivity of ConfiAI by moving a slider to different positions. The far-left position of the slider characterizes entries with the highest likelihood of correct detection, while the far-right position will display all entries
-
dynamic — allows setting a percentile (value from 1 to 100), which will display a certain portion/percentage of the most important vulnerabilities
-
- If there are two or more successful scans in a project, you can compare the current scan with any of the previous ones and display vulnerabilities according to status (if vulnerabilities are not tracked, change charset in the analysis settings and rescan the project)
- correlated to DAST findings
Filters will be applied after you click Apply.
Click on the vulnerability to display the complete list of detected vulnerability entries of this type. By clicking on the three dots on the right, you can change its severity level or status. You can also edit severity/status or a leave a comment for multiple vulnerabilities at once. To do this, switch to multiple vulnerability selection mode.
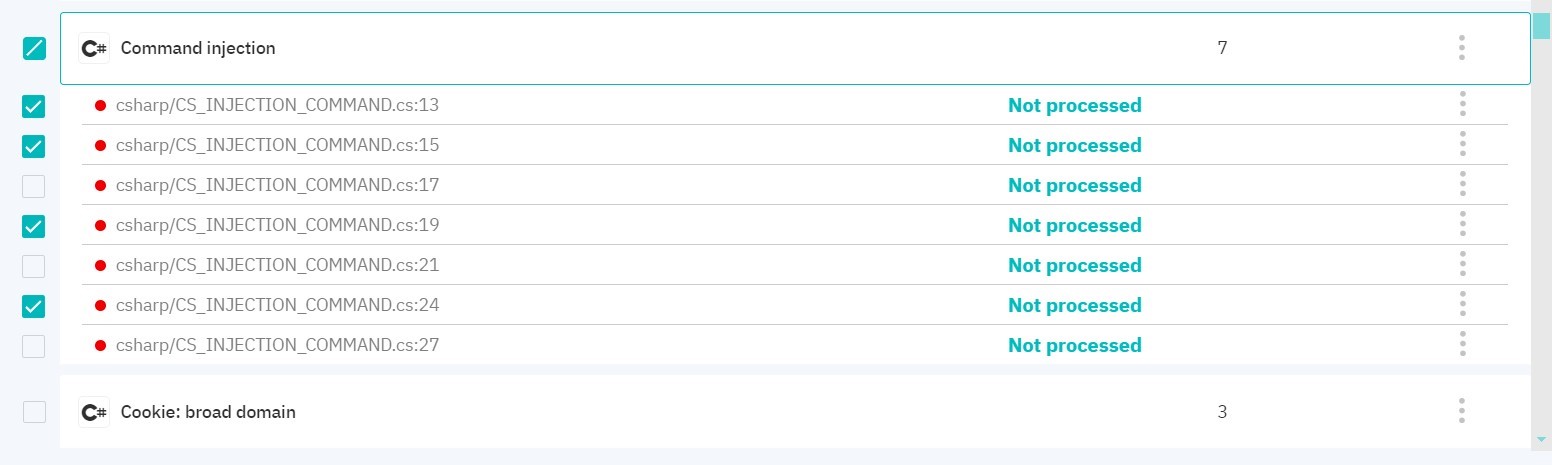
Figure 5.10: Multiple vulnerability selection mode
When changing vulnerability status and severity level, security score is recalculated. Vulnerabilities with the Rejected status are not taken into account when calculating vulnerability numbers and security score. When rescanning, your changes are saved.
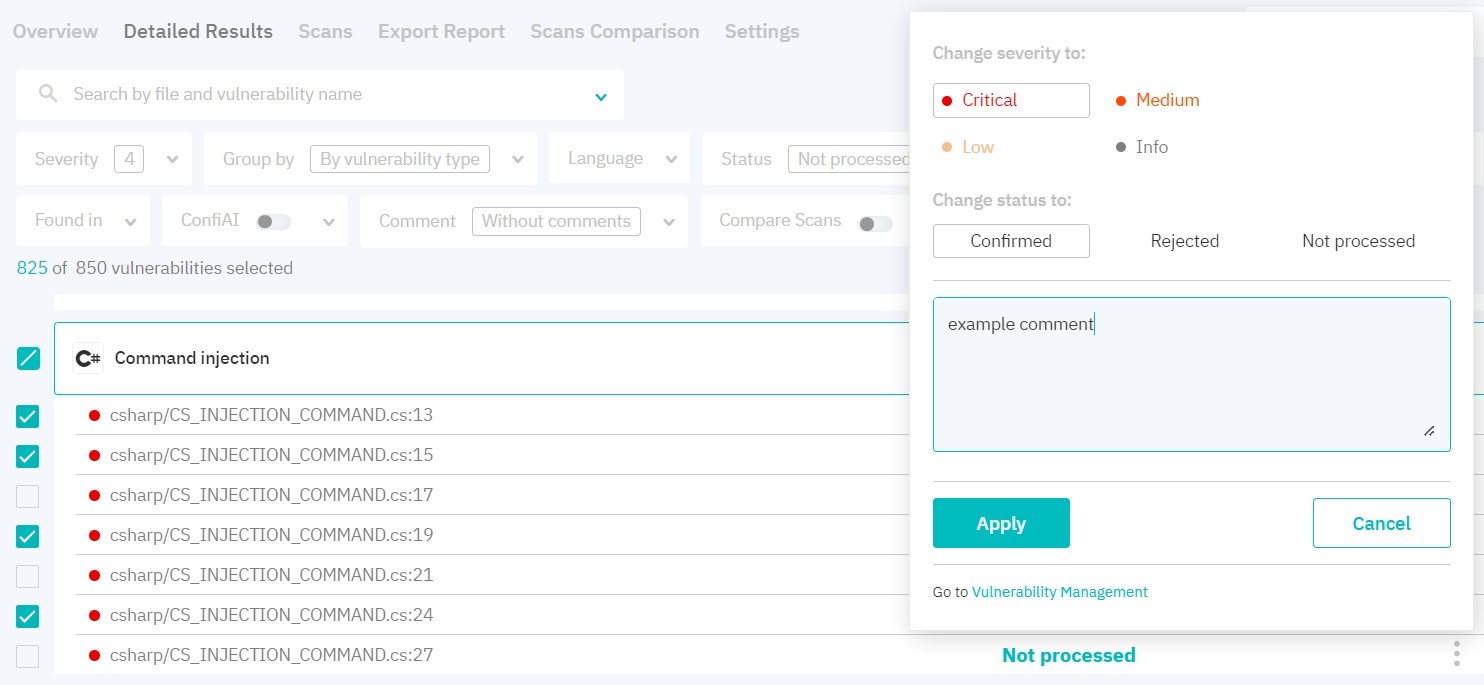
Figure 5.11: Vulnerabilities pack management
After choosing a certain vulnerability instance, the right part of the page displays the respective code fragment. To view information about the vulnerability in full screen, click the icon in the upper right corner, above the code fragment. The left part of the page will show information about the chosen vulnerability type: Description, Example, Recommendations on patching, Links to resources on this vulnerability type, and WAF set up instructions (for web apps).
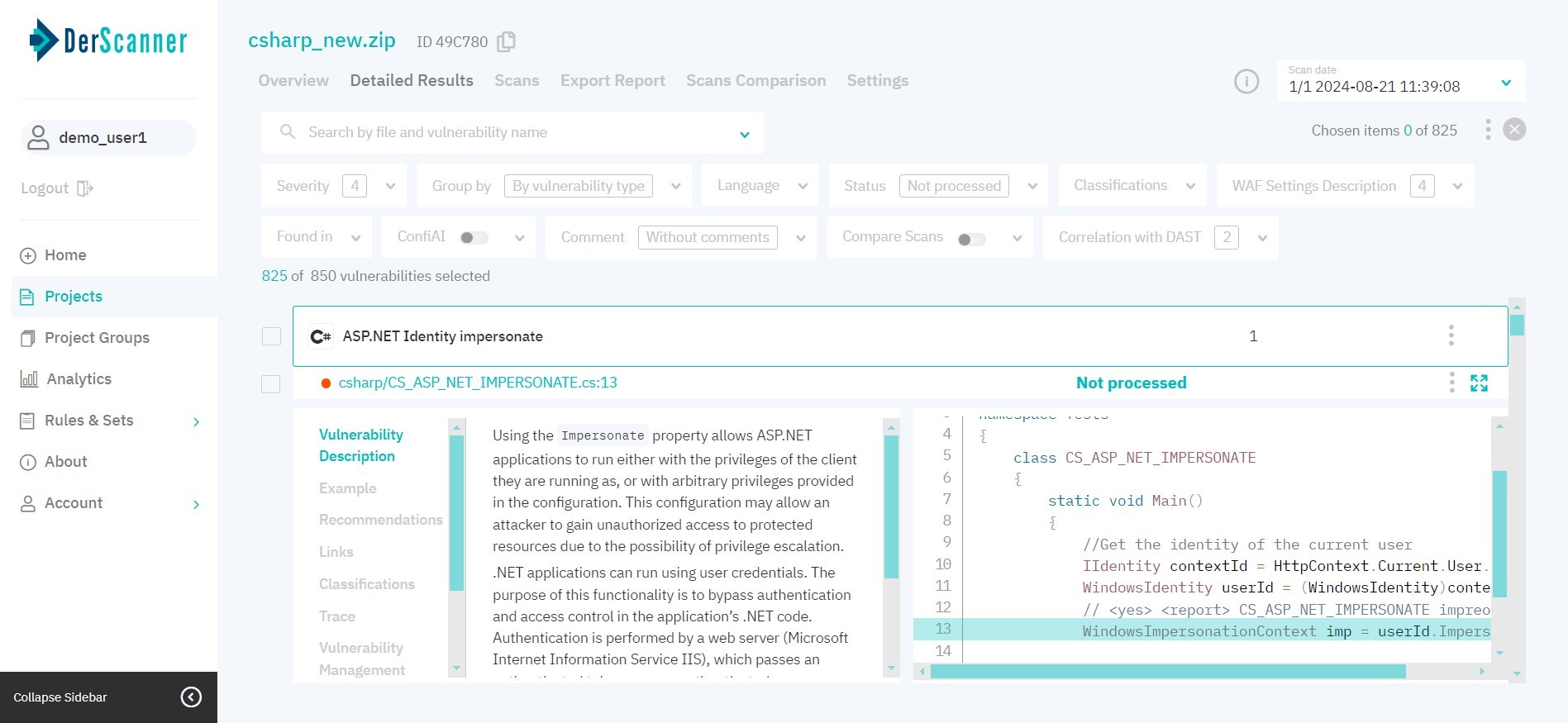
Figure 5.12: Vulnerability description
The Fix with DerCodeFix tab displays either a ready-made fix for the vulnerable code (if fix generation was enabled during the scan), or a Generate Fix button. To switch between the fix and the original code, use the toggle.
The Classifications tab displays respective items from CWE 4.0, CWE/SANS Top 25, OWASP Top 10, OWASP Mobile 10, OWASP ASVS, OWASP MASVS, PCI DSS 4.0, and HIPAA classifications.
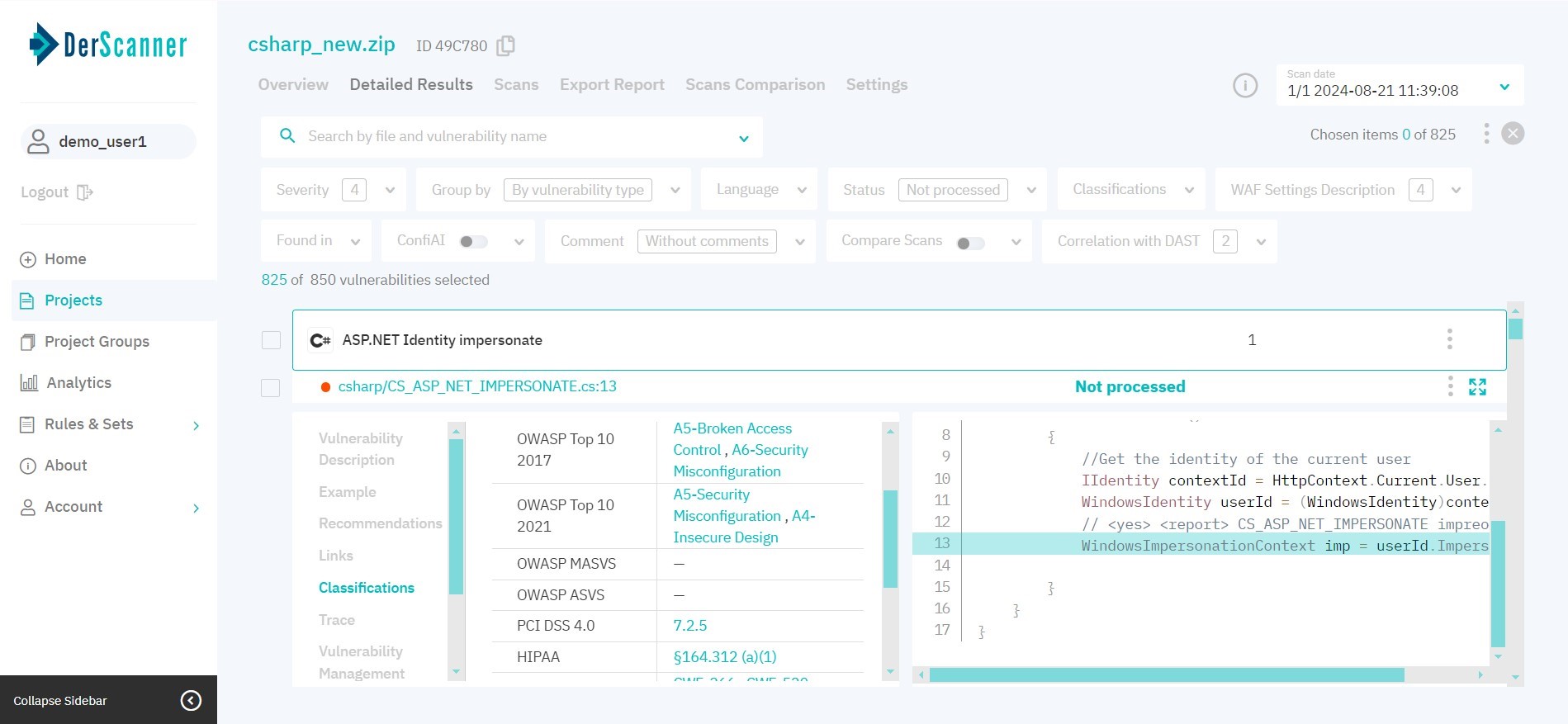
Figure 5.13: Classifications
The Trace tab is used to vissualize data propagation for vulnerabilities. Data propagation is represented as a chart with interactive elements which highlight a respective code fragment.
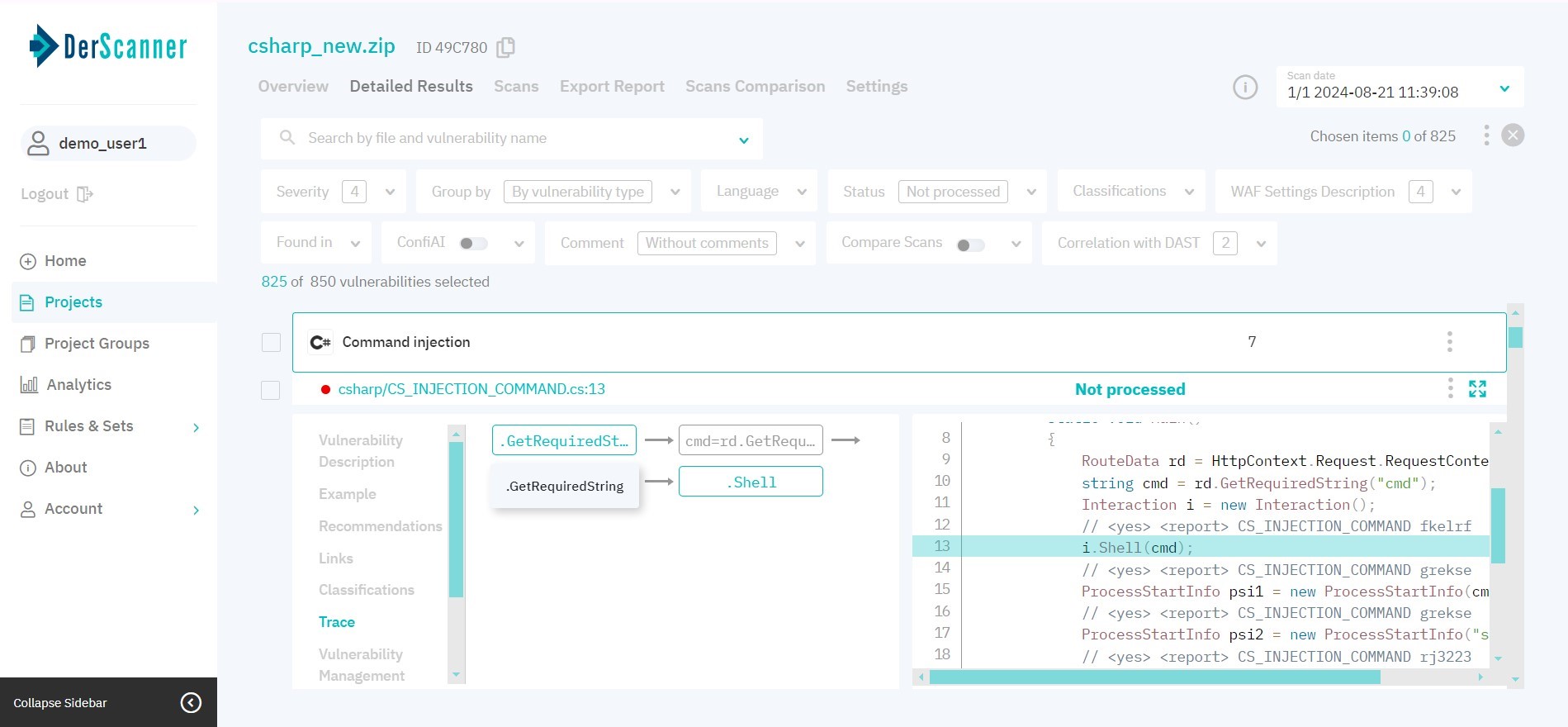
Figure 5.14: Trace
In the Vulnerability Management tab, you can change the severity level and status, add a comment to an entry, and view the event log accounting for all vulnerability related actions conducted earlier.
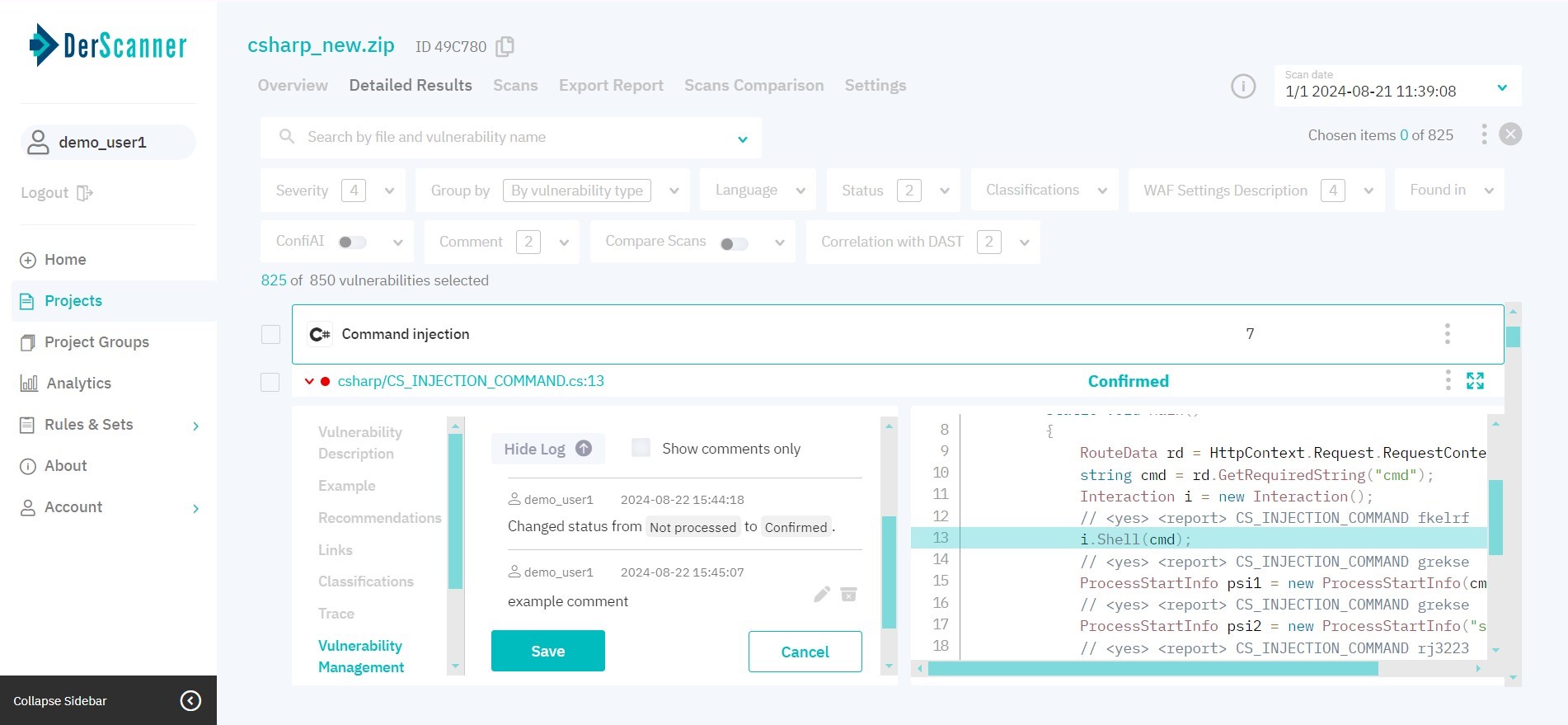
Figure 5.15: Vulnerability Management
Also, for each issue Confidence value is displayed on the tab. This parameter indicates the confidence of the ConfiAI module that this vulnerability is not a false positive. The greater the value of Confidence, the more likely the vulnerability is true positive.